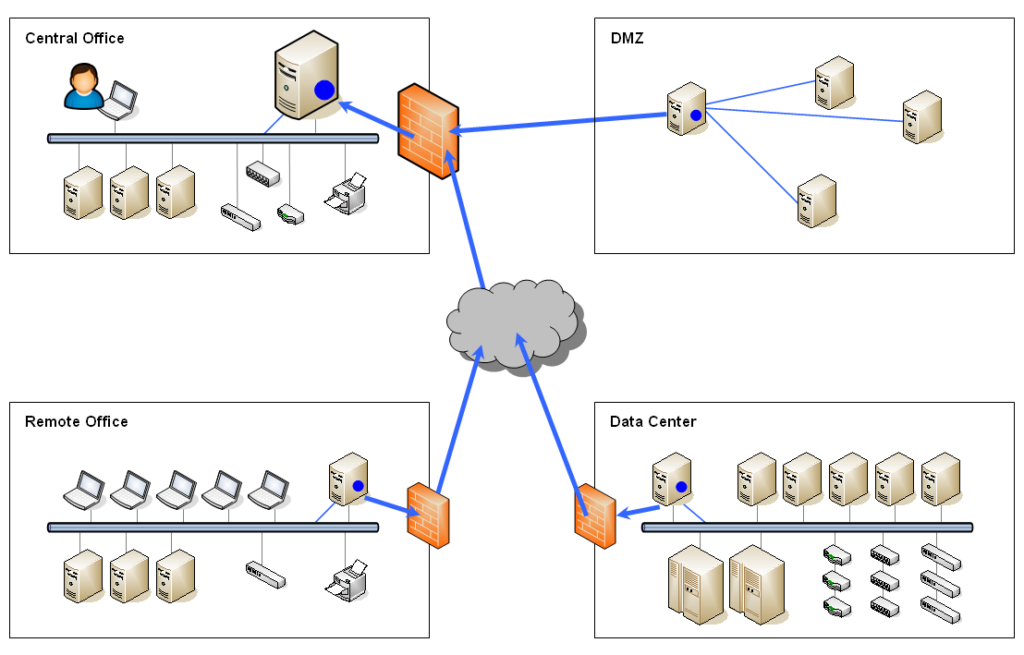
To meet the high demands on infrastructure and information technology from both an organizational and regulatory perspective, the focus today must be on much more than just the availability of digital systems, assets and data centers. While the classic SOC (Security Operation Center) remains an important building block for the operation and management of electronic system components, today’s requirements go far beyond device and continuity management. SIEM (Security Information and Event Management) and IDS (Intrusion Detection System) are also no longer the only security areas to protect the infrastructure being managed.
A machine-centric approach is formulated for a holistic view of requirements.