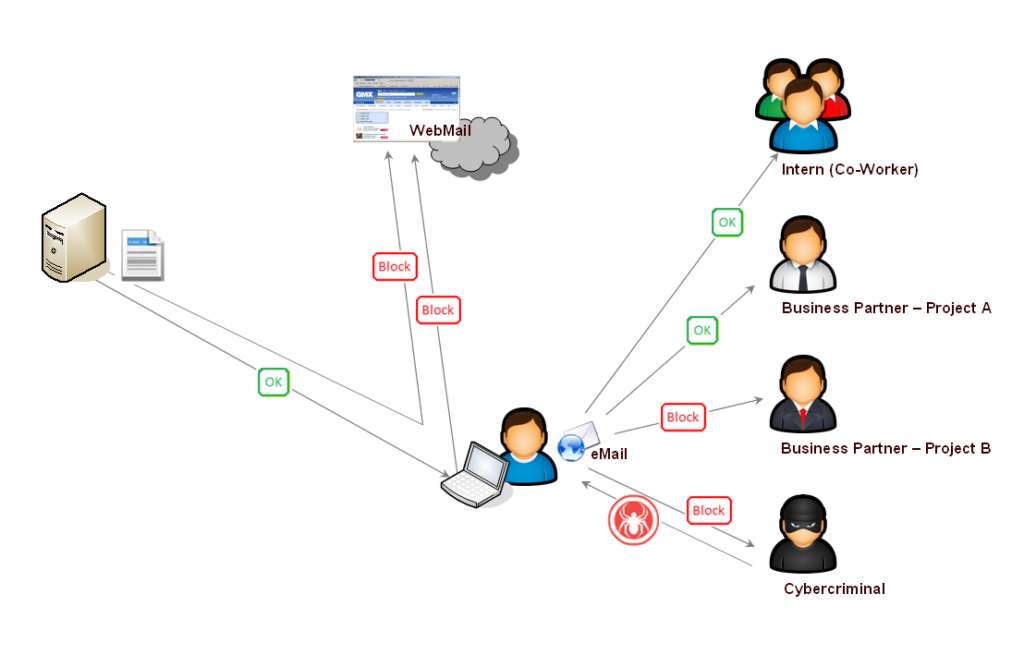
The data source is always shown to the left of the user, here a server with project data. A deeper and more detailed view, such as through data classification or content analysis, is not further elaborated for this simple example.
The recipients of the data are always shown to the right of the user. Here all possible destinations are represented, which the user can reach via the channel eMail. If there are further alternatives for the transmission, these options are shown in the representation above the user. If the alternatives are within direct reach of the user, then they are listed in the representation below the user. This last option does not exist for the eMail transmission channel, while such alternatives often exist in large numbers for other channels (file storage channel on various USB memory sticks, cameras or smartphones).
The Use Case describes that the user is allowed to edit data of all formats completely or in excerpts on the server, as well as to save these data on the local hard disk of his computer. Not allowed, blocked and with feedback to the user is any action that serves to distribute this data via WebMail. It is irrelevant whether the data is uploaded directly from the server to a WebMail portal or is first saved to the local hard disk.
The Use Case also describes how eMails are handled via the channel authorized by the company, depending on the recipient. In this example, all other employees of the company, as well as business partners in the respective project, can be reached. Business partners who are not involved in the respective project must not be informed. Again, when an attempt is made, sending is blocked and feedback is given to the user. Attached files as well as excerpted information in the message text are also taken into account. All recipients (To, CC, BCC) are always considered.
Intervention also takes place if an eMail is sent to unauthorized recipients due to fishing actions or other malware. It is irrelevant whether the user triggers the action accidentally or whether the malicious code previously foisted on the recipient triggers this task.
The enormous advantage for a user-centric approach at this point is the possibility of applying the superposition principle. Multiple, individually formulated Use Cases can be superimposed. Individual rules can be formulated in isolation to fit into a larger and more complex whole.
This superposition principle, known from physics, is used for linear problems in many areas (forces in classical mechanics, optics, but also states in quantum mechanics). The Framework used also avoids overlapping or contradictory rules.