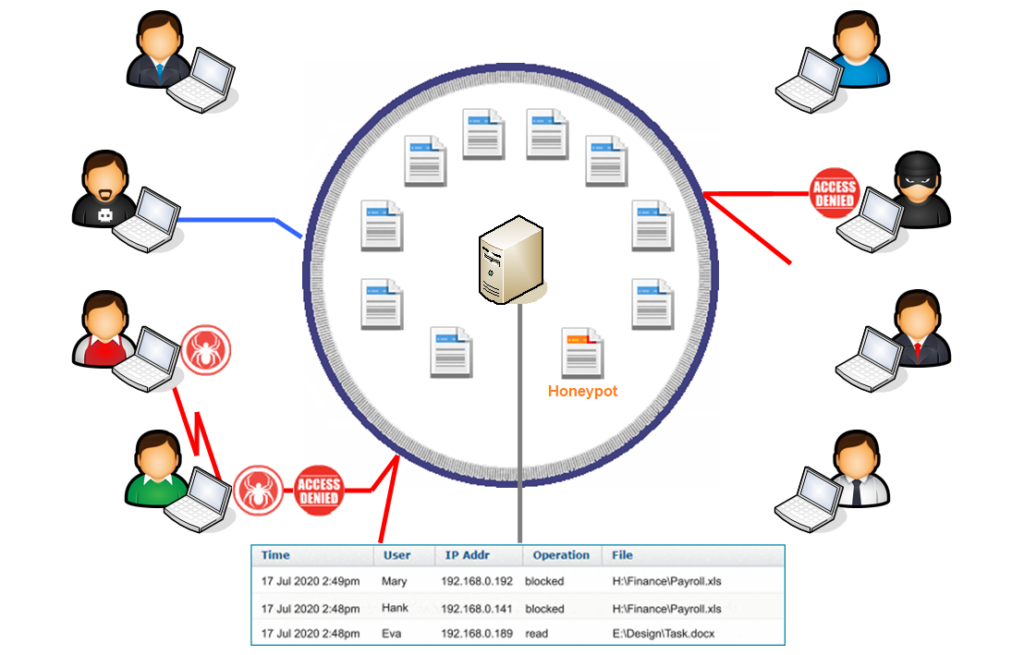
In order to meet the diverse requirements for integrity protection, it is necessary to go beyond isolated systems and multi-level access authorizations. If legal requirements even stipulate forensic proof of data integrity, far-reaching measures must be taken to protect sensitive company data from destruction, manipulation or criminally motivated third-party encryption. This applies to the central data sets in which the company stores its trade secrets as well as to the digital infrastructure on which this data is processed.
A data-centric approach is formulated for a holistic view of requirements.