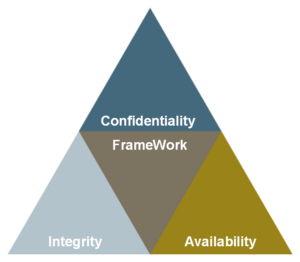
Compliance to Code refers to all measures to translate regulatory and legal requirements into clearly structured digital policies. Preferably, this measure does not exclusively support the area of availability of digital systems, facilities and data centers, but also integrates the areas of DLP and EIM into a SOC (Security Operation Center). The primary goal of C2C is to provide a clearly structured overview of the compliance of all digital assets and to present it in a form that is manageable for risk and compliance management.
A holistic view of intrinsic and extrinsic requirements, assets and risks, which captures and correlates operating states in real time as needed, offers significant advantages over isolated KPIs and their individually recorded threshold values. Complex tasks such as the permanent and automatic implementation of ISO 27000 controls can be elegantly captured, processed and managed.