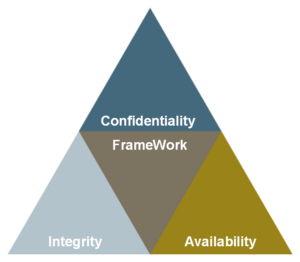
Within cyber security, the HKM framework forms the link between the three security objectives of confidentiality, integrity and availability and the areas of compliance, risk and governance that build on them. It contains an extremely efficient procedure for developing sets of rules for each sub-area of the C-I-A triangle and uses smart visualisations to define user-centric and data-centric approaches. For the development of a comprehensive data security solution, it serves to define the interfaces between the solution components.
Significance of the HKM framework for cyber security – Availability, Integrity & Confidentiality
In this way, systems for DLP (Data Leakage Prevention), EIM (Enterprise Integrity Management) as the components used in a classic data center for the permanent availability of the IT infrastructure and services, such as SIEM (Security Information and Event Management), IDS (Intrusion Detection System), MCD (Malicious Code Detection), etc. are united.
The framework binds the technology concepts into a common unit.
The framework also meets the requirements of centrally routing the notifications of the individual systems to an incident response system, where they can be comprehensively examined and immediately responded to. It is irrelevant which system is already available for this task in the SOC.
However, this stable foundation established in this way not only serves to align the solution components within cybersecurity, but also prepares further fundamental components for essential levels of action. The framework can be used to address governance, risk and compliance as well as data classification and the handling of personal data.
Significance of the HKM framework for cyber security – Governance, Risk & Compliance
By combining the two integrated, holistic approaches to cybersecurity (CIA triangle) and the management approach to facilitating the organization (GRC architecture), all technical and organizational processes can be mapped within a pyramid.
The link between the two models here is the Compliance module, which formulates clear intrinsic and extrinsic cybersecurity requirements in its definitions and whose protection goals are explicitly named in its specifications.
When the risk layer is built on top of this, and the governance layer on top of that, this arrangement in no way breaks up the direct interaction of the individual elements with each other. These layers always remain coupled via connections in the framework, which at its core is another pyramid whose base is anchored in the CIA triangle and whose apex also extends to governance. The objects for processes, strategy, people and technology are the supporting points within the framework and define and process the internal and external requirements as well as the risk appetite. All elements are viewed in an integrated, holistic and organization-wide manner.
Of course, both approaches keep all previous connections, relations and interactions with their objects.
The combination of the two approaches couples the theoretical-technical approach to cybersecurity with the organizational-strategic approach for a company. Here, for the first time, all prerequisites and goals are brought into connection.
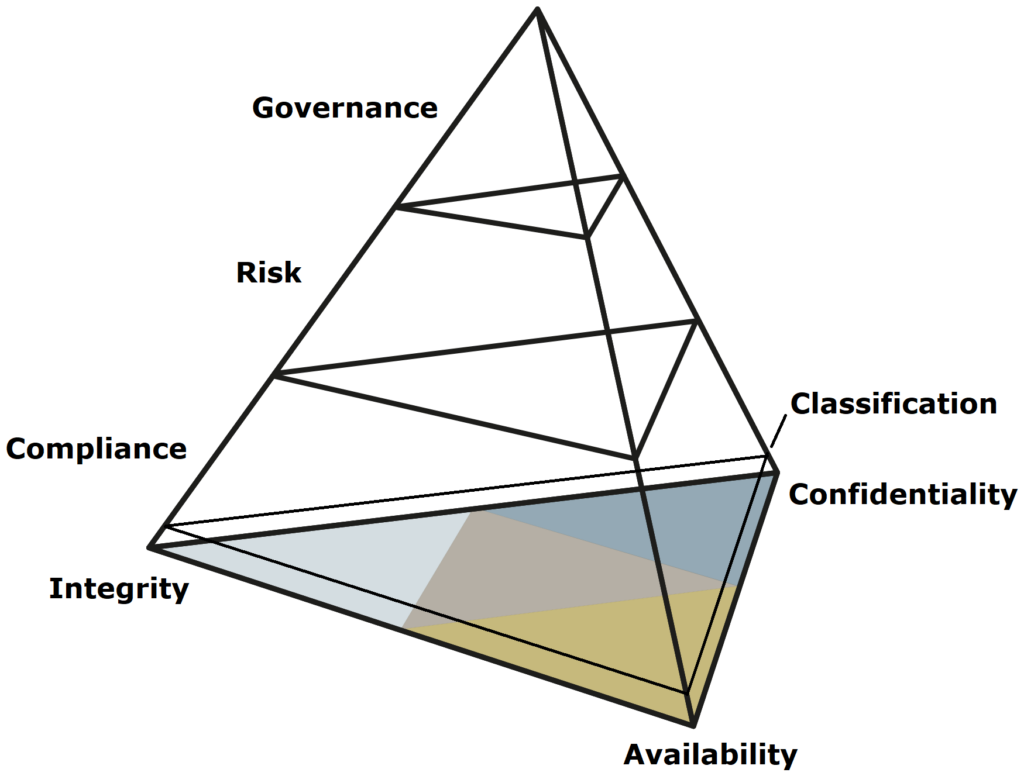
Data classifications can be represented as a separate layer. This layer is located within Compliance and can define the value of company data (e.g. trade secrets) or deal with a particularly sensitive set of data (e.g. personal data).
Internal definitions are made for sensitive company data. For personal data, external legal requirements apply.
In many companies, multiple classifications for one object are also conceivable.
The creative management of information technology, which can also always be understood as an organizational unit for the areas of confidentiality, integrity and availability, is detached from the form of the management approach for it. It can be determined by a very classical management approach through the principle of “operation and change”, waterfall or also agile methods with sprints. All of these approaches are governed by the cybersecurity protection goals. The form of management approach selected depends to a large extent on the structure and size of the company. A change in the management approach over time can be mapped at any time and does not affect the framework presented at any time.
Significance of the HKM framework for your company’s cyber security strategy
The HKM framework not only offers a basic structure that can be used to get started immediately, but also a variety of specific functions that are tailored to the needs of an integration project. In the area of IT security, this framework provides a collection of proven security measures, processes and tools. It provides clear guidance on how to identify and close security gaps and helps to implement security protocols that meet the individual requirements of your organisation.
In addition, the HKM framework helps to implement security policies efficiently without losing the overview. Automation and standardised procedures ensure that all important steps are followed, saving time while minimising risk. In a world where threats are constantly evolving, this framework allows you to stay up to date and respond quickly to new challenges.
Furthermore, the framework makes proven best practices such as ITIL, PRINCE2 and other recognised standards available to you. These methods are used specifically to identify the key aspects that are decisive for the implementation of regulations such as ISO, GDPR, NIS-2 or the Cyber Resilience Act. The framework is based on a clear focus: it helps you to concentrate on the core tasks in cyber security without getting lost in the details of the many requirements. You receive precisely the tools and approaches you need to implement your security strategy in an efficient and targeted manner.
The framework has a modular structure so that it can be flexibly customised to the specific needs and certification objectives of your company. Regardless of whether you are aiming for a specific ISO certification or have to meet the requirements of the Cyber Resilience Act or NIS-2 – you can access this modular system in a targeted manner. The tasks and processes you have defined are analysed from the perspective of the relevant regulations and supplemented where necessary. This means that you don’t have to completely redo your existing work. Instead, you can expand and customise existing processes with additional modules. This keeps your work efficient and future-proof, while you continue to ensure compliance with the relevant requirements.
With the HKM framework, you not only invest in compliance with regulations, but also ensure a clear return on investment. The modular structure allows you to reuse and refine the work you have already done, which avoids duplication of work and utilises your resources efficiently. On the timeline, you benefit from rapid adaptation to new requirements without having to relaunch existing projects. Instead, you build on your previous progress, expand it in a targeted manner and optimise your processes. This not only ensures the smooth integration of new requirements, but also maximises your investment in cyber security and increases the overall efficiency of your company.
Our framework is designed not only to protect your investments and increase efficiency, but also to actively engage your employees. It provides clear, modular guidance that allows your team to integrate and refine existing processes without having to start from scratch.
This structured approach ensures that employees are optimally trained and that the new requirements can be implemented smoothly. This not only promotes acceptance and motivation within the team, but also ensures that your overall security strategies are implemented efficiently and sustainably.
