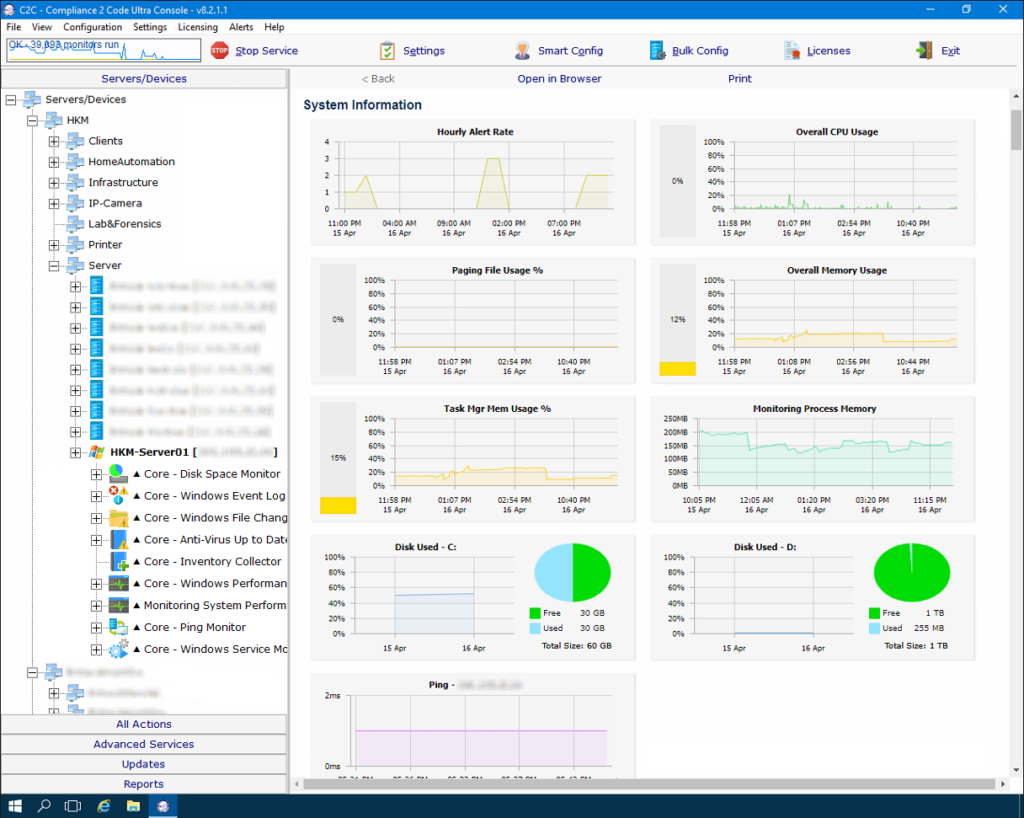
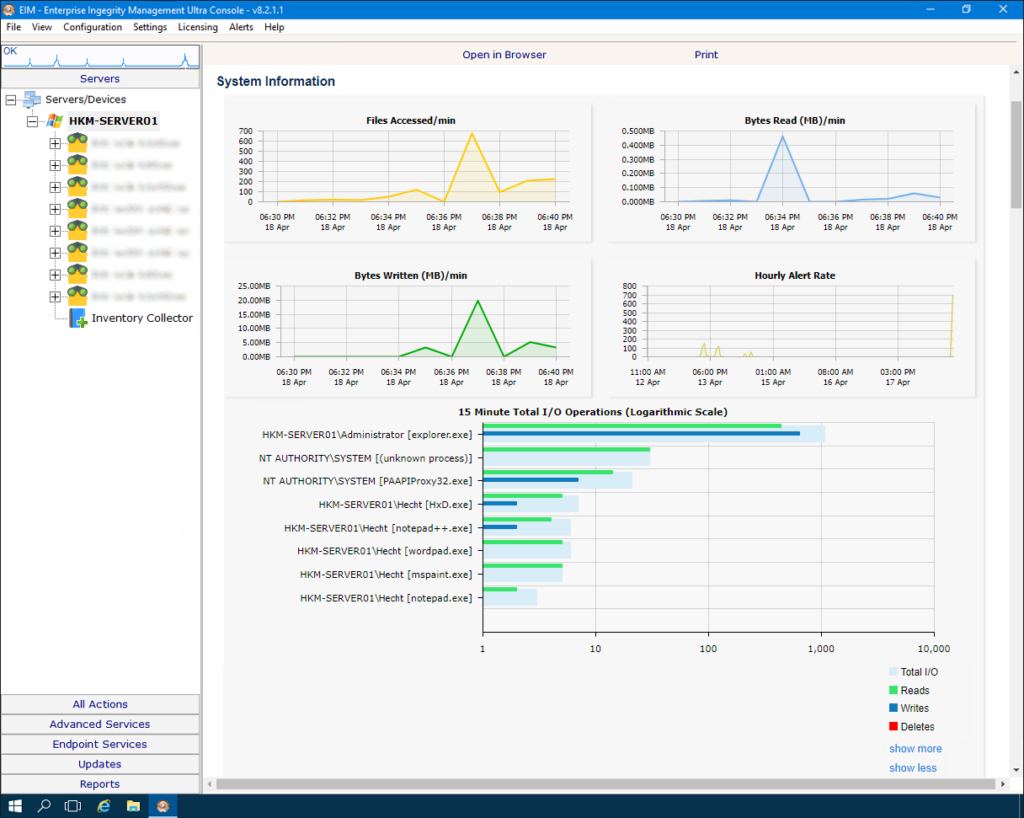
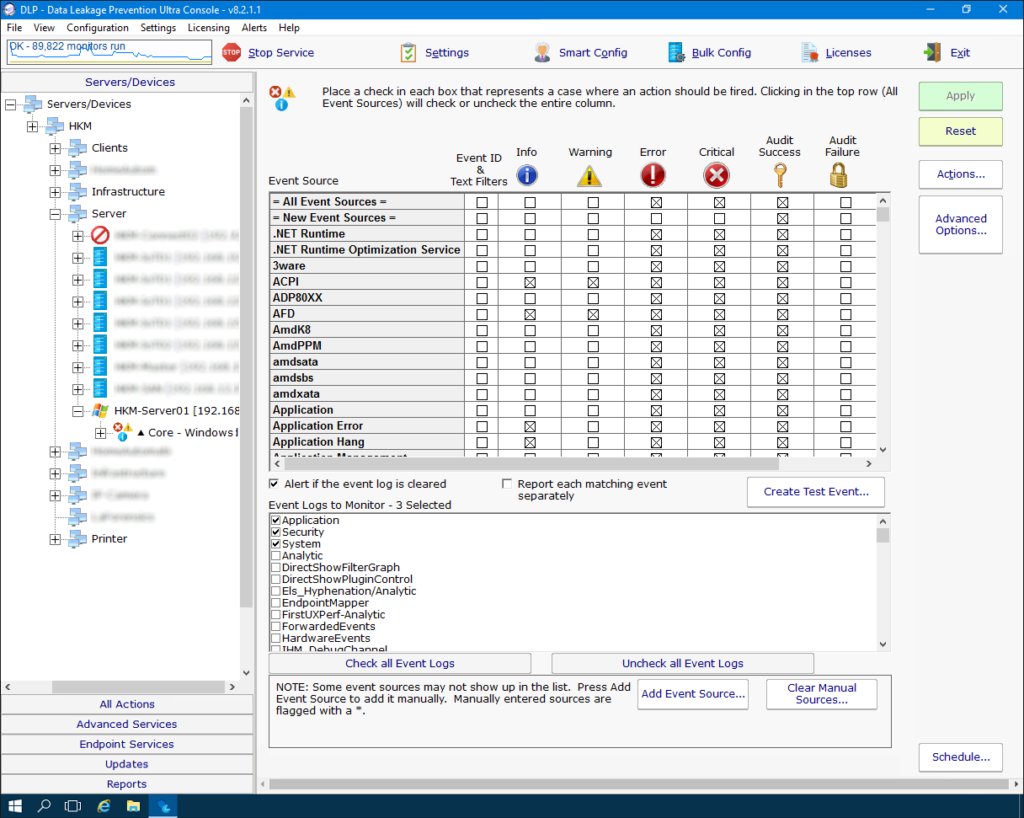
Products & services for intellectual property protection
The highly scalable products and services for the protection of intellectual property interlock seamlessly. The realization of the implementation extends to on-premise, IoT and cloud, as well as hybrid solutions from these infrastructures.